Troubleshooting SAML error codesWindows authenticationOAuth authentication
Overview
When configuring SAML 2.0 as your authentication protocol, you may face different error messages regarding its configuration. This article shows the possible error messages as well as their respective solutions.
Before You Start
It is recommended to enable the authentication traces. To enable the authentication traces, go to your project in Bizagi Studio. In the configuration tab, click Tracing.
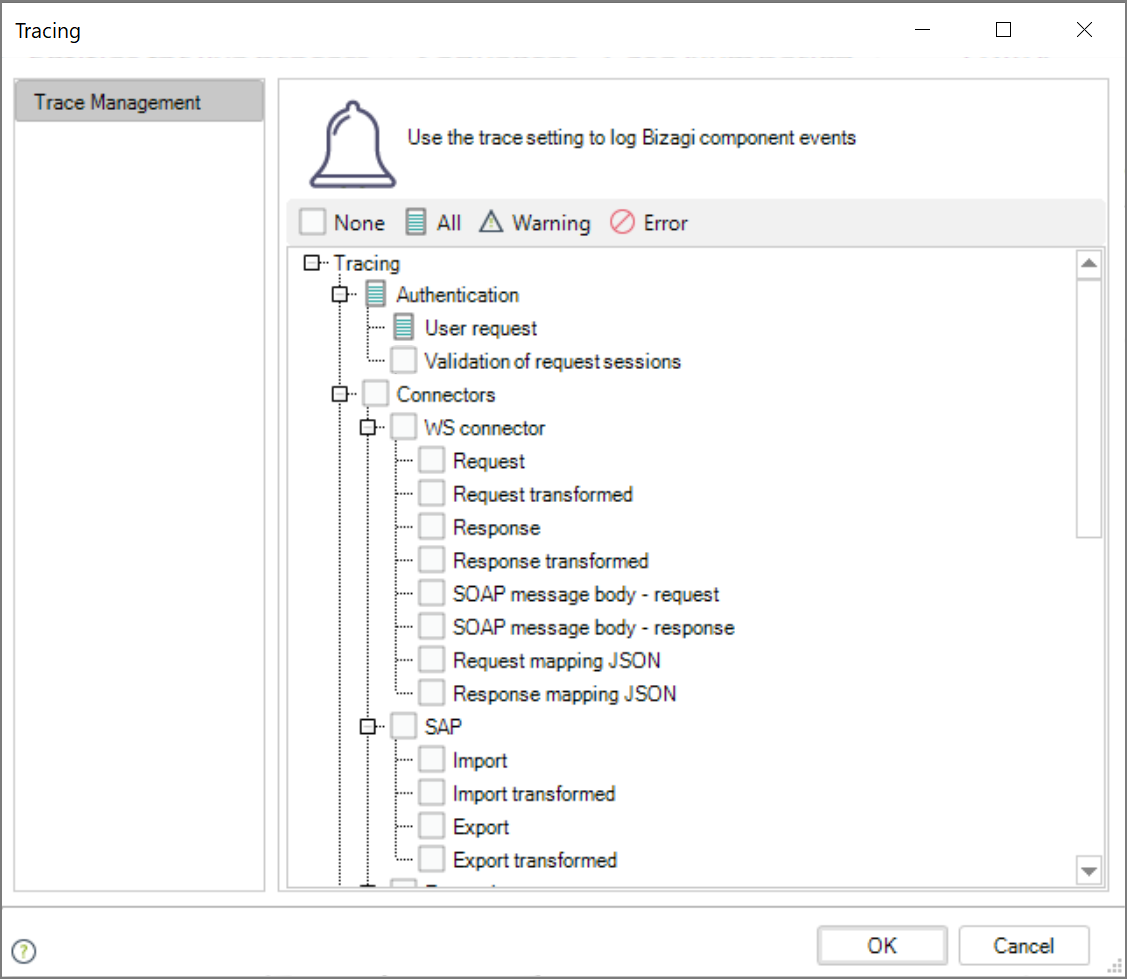
Then, enable the logs for Authentication -> User request.
Troubleshooting SAML Authentication Codes
| Code | State | Cause | Solution |
|---|---|---|---|
| 3000 | saml2_error | An unhandled exception appears during the configuration process or when receiving SAML 2.0 messages when trying to connect with non-supported Identity Providers. | - If the error "Invalid algorithm specified" is registered in the traces, verify that the certificate loaded in Bizagi Cloud used to sign supports the algorithms SHA-256 or SHA-1. Ensure that the certificate supports SHA-256, SHA-384, and SHA-512. Use "Microsoft Enhanced RSA and AES Cryptographic Provider" for strong algorithm support. - If the error "No Identity Provider supporting SAML binding REDIRECT found in metadata" is registered, ensure the Single Log Out endpoint is configured correctly in the IdP. - If the error "The specified network password is not correct" is registered, generate a new certificate following Bizagi guidelines. |
| 3001 | binding_saml2_error | Occurs when an unknown binding was registered, or when the binding is not supported for an Identity provider. | Bizagi supports the following bindings for SSO and SLO: - HTTP Redirect Binding - HTTP POST Binding Ensure the Identity Provider uses one of these bindings, as unsupported bindings like HTTP Artifact Binding or SAML SOAP Binding may cause this error. |
| 3002 | idp_endpoints_saml2_error | The Identity Provider (IdP) endpoints are null or don't exist in the IdP metadata file. This might happen because: - In the path Expert -> Security -> Authentication in Bizagi Studio, the path to the IdP file was configured incorrectly. - The IdP metadata file is incomplete or has errors. | Make sure that the metadata file used in the setup is correct. |
| 3003 | service_provider_not_set_saml2_error | The Service Provider is null or wasn't configured. | Make sure that the following properties are completed: - Organization Name - Technical email contact adress - Organization URL - Service Provider URL |
| 3004 | metadata_location_not_found_saml2_error | The IdP metadata file directory or URL cannot be located. | Verify in in Bizagi Studio in the path Expert -> Security -> Authentication, the Identity Provider Metadata File Path property. Make sure that it is well configured and that the file is accessible by Bizagi. |
| 3005 | invalid_file_signature_saml2_error | The IdP file signature cannot be verified. | Make sure that the algorithm used by the IdP to sign the file's metadata is supported by Bizagi. The supported algorithms are SHA-1 and SHA-256. Also, if the file was edited, check for possible errors. |
| 3006 | metadata_configuration_saml2_error | This error might happen because: - The binding used is not supported by Bizagi - The IdP's URI is not valid | - Verify that the binding included by the IdP is supported by Bizagi. Bizagi supports the following bindings for SSO and SLO: - HTTP Redirect Binding - HTTP POST Binding - Verify in in Bizagi Studio in the path Expert -> Security -> Authentication, the Service Provider URL property. Make sure that this property has the URL where Bizagi was deployed. |
| 3007 | sso_binding_not_supported_saml2_error | The binding used for the Single Sign On (SSO) is not supported | Verify that the binding included by the IdP is supported by Bizagi. Bizagi supports the following bindings for SSO: - HTTP Redirect Binding - HTTP POST Binding |
| 3008 | slo_binding_not_supported_saml2_error | The binding used for the Single Log Out (SLO) is not supported. | Verify that the binding included by the IdP is supported by Bizagi. Bizagi supports the following bindings for SLO: - HTTP Redirect Binding - HTTP POST Binding |
| 3009 | invalid_data_time_assertion_saml2_error | The assertion valid time does not met the SAML-Core specification. Valid time does not meet the SAML-Core specification when: -The assertion is read before the valid time. - The assertion is read after the valid time. | •Make sure that the assertion is read in the allowed time window. If it is read before or after, the error will persist. •Verify that the IdP is generating the time values for the assertions as specified in section 1.3.3 of the SAML-Core document. |
| 3011 | metadataidp_missing_entityid_saml2 errormetadata_idp_missing_entityid_saml2_error | The IdP metadata file does not have the entityID attribute. | Make sure that the IdP metadata file includes the entityID attribute with the server ID. |
| 3014 | metadata_load_error_saml2_error | The IdP metadata file cannot be loaded. This might occur because it is empty or has errors. | Verify that the IdP file: - Is not empty - Does not have special characters - Has the XML structure that meets the SAML 2.0 specification |
| 3015 | saml2_configuration_not_found_error | The SAML 2.0 configuration is not found in the Bizagi Cloud database. This might happen when migrating between Bizagi versions or if there are errors in Bizagi's internal metadata, or if there is only one active user in the database and is trying to obtain the SAML metadata from Bizagi. There must be at least two active users to use the SAML 2.0 protocol. | Contact Bizagi's technical support. |
| 3016 | private_key_not_found_error | The private key of the certificate is not found. This happens when a certificate is loaded with the public key, but not with the private key. | Generate and load the certificate that includes the private key. Then, load the certificate in Bizagi Studio in the following path: Expert -> Security -> Authentication in the property Signing certificate. Finally, configure the password needed for the private key in the following path: Expert -> Security -> Authentication in the property Signature certificate password. |
| 3017 | response_not_contain_an_InResponseTo_error | The response message received does not contain the InResponseTto attribute. This happens when the message sent to /saml2/assertionConsumer does not have the proper structure. | Look for the IP or the URL from which the requests are being sent and fix the issue in the external application. |
| 3019 | status_assertion_saml2_error | You may receive one of the following responses from the IdP: •urn:oasis:names:tc:SAML:2.0:status:Requester: the SAML request could not be processed due to an error in the message creation in Bizagi. •urn:oasis:names:tc:SAML:2.0:status:Responder: the SAML request could not be processed due to an error in the IdP •urn:oasis:names:tc:SAML:2.0:status:VersionMismatch: the SAML request has an incorrect version or a version that is not supported by the IdP. | Look in both Bizagi and the IdP authentication logs to determine the issue. Possible solutions for this problem are: •If the IdP does not trust in the certificates sent by Bizagi, export the certificates public keys and install them in the IdP. •If the IdP does not support the algorithm used by Bizagi to sign the certificate, make sure to configure the same algorithm in both Bizagi and the IdP. •Validate that both Bizagi and the IdP have a correct configuration. |
| 3020 | decrypted_assertion_error | The assertion could not be decrypted. | Verify that you are using complete encryption for the assertion. Bizagi does not support encryption by parts or attribute encryption. |
| 3021 | locate_assertion_decryption_error | It is not possible to locate the key to decrypt the assertion. This happens when the IdP sends an assertion to Bizagi with the EncryptedAssertion element, but it is not possible to locate the EncryptedKey element. | Make sure that the encryption option is configured in the IdP and that Bizagi's certificate is installed in the IdP. |
| 3022 | format_saml2_error | The assertion does not comply with the format validations. | Look in the authentication logs in Bizagi for the element that could not be validated and fix its format. |
| 3023 | assertion_signature_could_not_be_verified_error | The assertion signature sent by the IdP could not be verified. | •Make sure that the algorithm used by the IdP to sign the file's metadata is supported by Bizagi. The supported algorithms are SHA-1 and SHA-256. •Make sure that the certificate used for the signature is valid and that corresponds with the one specified in the metadata file. •Verify that the IdP is configured to sign the messages sent to Bizagi. |
| 3024 | assertion_is_expired_error | The assertion expired or could not be validated. This happens when the attribute NotOnOrAfter, from the element SubjectConfirmation could not be validated. This might be because: •The assertion expiration time was configured too short. •The time configured is 0. •An expired assertion is being used. | Check for the IdP configuration and adjust the assertion time. |
| 3026 | assertion_must_contain_one_issuer_error | The assertion does not comply with the format validations because the (issuer) element is missing. | Vefify that the IdP includes the (issuer) element when generating the assertion. |
| 3029 | assertion_name_id_not_found_error | The subject element in the assertion response does not have the NameID element. This element is used to identify the user and must be validated by Bizagi. | Make sure that the IdP includes and maps correctly the NameID element in the assertion response. This element must have the user's username and must be included in one of the following formats: •domain\username •username@domain |
| 3030 | logout_saml2_error | The session cannot be closed because the user does not have an active session. A user session is identified in Bizagi with the SessionIndex attribute, in the AuthnStatement element. When a user logs out, Bizagi sends the SessionIndex to the IdP so that the session can be closed. However, the error appears when the IdP cannot find the specified SessionIndex. This may happen because: •The session in the Work Portal was closed automatically due to user inactivity. •The IdP URL was changed while the user was working in the Work Portal •The IdP was restarted, and the contexts' states and the server sessions were not persisted. | Erase the cookies from your browser and sign in again. |
| 3031 | single_logout_unknown_idp_error | a logout request is received from an unknown or an untrusted IdP. The requests sent to Bizagi must come from a registered IdP. | Make sure that the IdP metadata file is correct and that the requests are being sent from the correct IdP. |
| 3032 | signature_not_present_error | The incoming message is not signed | Make sure that all the messages that the IdP is sending to Bizagi are signed. |
| 3033 | unsupported_request_type_error | The HTTP request has a non supported method. Bizagi supports GET and POST HTTP requests. Other methods are not supported. | Verify that the IdP is using a method supported by Bizagi. |
| 3035 | logout_request_is_malformed_error | The logout request is not complete. The SAMLResponse or the SAMLRequest parameter is missing. | Make sure that the logout request is being sent to the correct endpoint and that the parameters specified are complete. |
| 3036 | signature_algorithm_not_supported_error | The algorithm used to sign the messages and the assertions is not supported by Bizagi. | Make sure that the algorithm used by the IdP to sign the file's metadata is supported by Bizagi. The supported algorithms are SHA-1 and SHA-256. |
| 3037 | sha256_algorithm_saml2_error | This happens when the SHA-256 algorithm is invalid or is not supported. | Verify that Bizagi is using version 4.5 of the .NET Framework, in versions lower than 4.5 the validation of signatures with the SHA-256 algorithm generate an error. |
| 3038 | encryption_key_not_found-error | The encryption certificate was not found in the database. This happens when the assertion encryption option is enabled in Bizagi Studio, but no certificate is uploaded to do the encryption. | In Bizagi Studio, go to the following path: Expert -> Security -> Authentication and make sure that the properties Encription certificate and Signature certificate password are properly filled out. Take into account that the certificate must be in a P12 or PFX format and the private key must be protected with a password. |
| 3039 | assertion_not_found_saml2 | Bizagi received in the endpoint /saml2/assertionConsumer a request that does not have an assertion or a SAML token. | Make sure that the Service Provider in the IdP is properly configured. |
| 3041 | signing_certificate_not_found_saml2 | The certificate needed to sign the messages generated by Bizagi is not found. | Generate the certificate that includes the private key. Then, in Bizagi Studio, go to the following path: Expert -> Security -> Authentication and make sure that the properties Signing certificate and Signature certificate password are properly filled out. if the Signing certificate is missing, load the certificate that you generated and finally, configure the password needed for the private key in the following path: Expert -> Security -> Authentication in the property Signature certificate password. |
| 3042 | encryption_certifcate_not_found_saml2 | The certificate needed to encrypt the messages generated by Bizagi is not found. Bizagi gives you the option to encrypt the messages sent to the IdP. If this option is enabled, you need to generate a certificate to encrypt the messages. | Generate the certificate that includes the private key. Then, in Bizagi Studio, go to the following path: Expert -> Security -> Authentication and make sure that the properties Encryption certificate and Encryption certificate password are properly filled out. To do this, load the certificate that you generated in the Encryption certificate property and configure a password in the Encryption certificate password property. |
| 3043 | too_short_idle_session_timeout_configurated_in_bizagi | The session time in Bizagi is lower than 1. | Configure the session time in Bizagi with a value equal or higher than 1. |
| 1150 | user_not_found_error | The user does not exist in Bizagi. | Users need to be created or synchronized before they can log in to the Work Portal. |
| 1155 | assertion_saml2_email_duplicate_error | The email account is assigned to more than one user. | Update the WFUSER table so that every user has a unique email adress. |
| 122 | assertion_saml2_user_not_enabled_error | The user is not enabled in Bizagi. | Log in to Bizagi with the Administrator account and enable the specified user. |
| 123 | assertion_saml2_user_locked_account_error | The user is blocked in Bizagi. | Log in to Bizagi with the Administrator account and unblock the specified user. |